AS with many other things in this world, there’s always a little of the bad that comes with the good and vice versa. Take the COVID-19 pandemic for example. Although the aftermath has been devastating with millions of lives and businesses lost, it managed to force the country to take its automation and digitalisation efforts more seriously.
When it comes to the manufacturing industry, automation is especially crucial. Not only does it reduce the number of workers having to handle tedious tasks, it helps the facility maintain its efficiency and even improve productivity.
However, it opens up the doors to unseen threats like malicious cyberattacks. These types of infiltration are not limited to the IT segment or the desktops and laptops utilised on site. It encapsulates the machines used in the production line and the industrial control systems (ICS) used to control the production process.
By leaving these machines vulnerable to cyberattacks without proper precautions in place, it’s the same as handing the keys of your whole manufacturing plant to the attackers.
In an exclusive interview with Quantum Computing CEO Kumaran Sukumaran, he mentioned that most manufacturers rely on traditional IT cybersecurity to protect their operational technology (OT) as well.
“A regular anti-virus and IT grade firewall is not adequate to protect OT as any intrusions on site or remotely can shut down operations, causing tremendous amounts of money loss and cause potential harm to the workforce,” he cautioned.

Kumaran cited a report by the European Union Agency for Cybersecurity that revealed:
- Suppliers either did not know or did not report how they were compromised in 66% of supply chain attacks.
- Advanced persistent threat (APT) groups were credited with carrying out 50% of supply chain attacks.
- Exploiting trust in the supplier accounted for nearly 62% of attacks on customers.
He also highlighted that from January to December last year, MyCERT reported a total of 10,016 cyber-related cases, risking the country to potentially lose RM51 bil in 2024 from cyber security incidents.
“Despite these numbers which are tabulated and announced, our concern is on the fact that manufacturers may not even be reporting the incidents to the authorities,” Kumaran voiced out.
Some of the reasons as to why the suppliers would choose to leave the incidents unreported include:
- They consider it to be an IT attack and they are not aware of OT cyber security
- Need to protect their credibility in the supply chain
- Fear of being transparent about vulnerability to attacks
Knowing the enemy
“One of the biggest problems Malaysian companies are facing is that they simply do not understand what to protect against, with 50% believing an attack would be carried out by a competitor while just 17% thought it was more likely to come from security specialists,” Kumaran explained.
It also does not help that a majority of manufacturers are either unaware or confused about what it means to be secure in the cloud, especially when it comes to next generation cyber threats.
Pandemic challenges in addition to day-to-day production issues also seem to push OT cybersecurity way down the priority list, enforcing the believe that it is a ‘nice to have’ feature, but not a ‘must-have’.
From the interview, Kumaran explained several examples of emerging next gen security threats that could affect the OT are:
- Advanced persistent threats (APTs) target specific individuals or even companies with the intention of stealing data, usually intellectual property (IP). These types of attacks are long term and can last months or years until they eventually gain access to what they were looking for. Silent crawlers can be present in the system and lie dormant until it detects the information it wants to steal. Once an APT is discovered, it’s usually too late. This is why real-time monitoring is essential.
- Supply chain compromise enable the hackers to take advantage of suppliers by intercepting shipments or inserting hardware components with malware that then spreads throughout the entire network, which could be devastating to the operations in entirety and affect the company’s reputation and trustworthiness.
- Crippling malware and viruses have evolved over the years with the intent to interfere with the normal business functions for a targeted facility. In its many forms like worms, Trojan horses, rootkits, spyware, adware, and shareware, these malware can easily cripple the production line.
- Remote access trojans (RATs) are backdoor programs installed on personal computers or servers that provide a hacker access to the system in order to control it remotely, allowing the attacker to perform malicious tasks such as viewing screen contents, controlling the mouse, recording keystrokes, stealing passwords or other data, downloading/uploading files, etc. This intrusion does not have to be remote and via the cloud. It can be due to storage devices like thumb drives or hard disks plugged into systems in the plant.
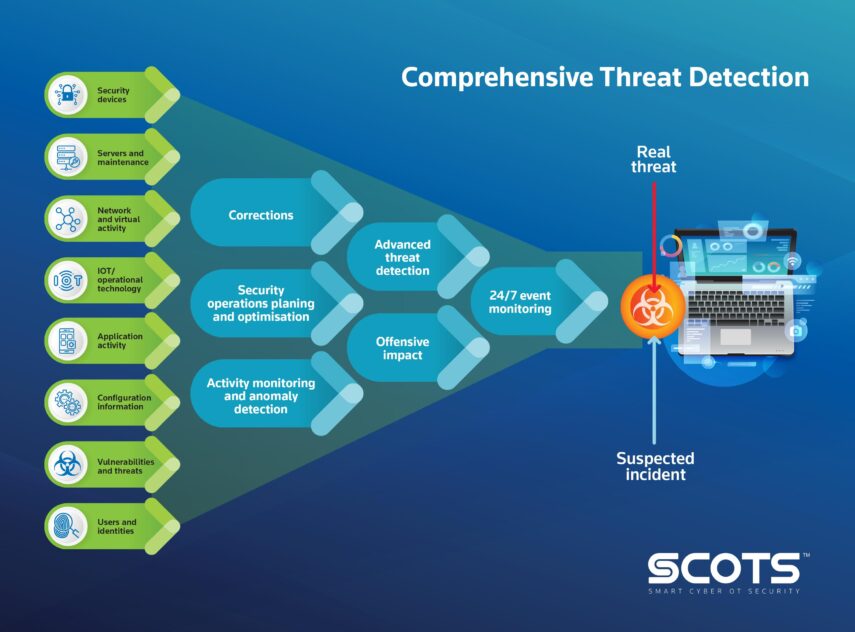
More needs to be done
With the belief that the lack of awareness in cybersecurity being one of the reasons why Malaysia’s Industrial Revolution 4.0 (IR4.0) initiative is not as accelerated compared to other countries, Kumaran stressed the need for more comprehensive education from the line automation right up to the security concerns and how to overcome it.
“IR4.0 is similar to the computer and the more popular Internet phases experience by the world. We all start with the benefits and multiple features and security concerns always comes into play in the later stages,” he said.
Kumaran also advised manufacturers to ensure their automation solution providers are not relying on their existing IT security systems to secure across their automation solutions.
“We need to improve our awareness and adoption of security for OT just as much as IT. We have to accelerate our adoption rate in order for us to remain attractive as a manufacturing and supply chain hub,” he added.
According to Kumaran, there are several things that manufacturers can do to efficiently protect their facilities from cyber threats.
The first is to ensure that everyone in the company is aware of the dangers and consequences of a cyber-attack. Employees should be trained on how to identify and protect themselves from common cyber threats, and how to respond if they are targeted by a hacker.
Manufacturers should also have a plan in place for responding to a data breach or cyber-attack, and ensure that all employees are familiar with the plan.
In addition, manufacturers should install security software and updates on all devices used in the production process, and make sure that all networks are properly protected.
Without a doubt, this means that manufacturers should invest in specialised cybersecurity tools that can help to monitor and protect their facilities from cyber threats.
“(Manufacturers) need to identify their challenges which can include building a clear understanding of IT vs OT, understanding the level of risk their business is vulnerable to, and coping with the lack of compliance regulation for OT cybersecurity with proactive efforts towards developing internal guidelines,” he ended. – March 24, 2022